CMMC: How to Know Which Level and Controls Applies to You
What CMMC Really Measures
- Federal Contract Information (FCI): basic information about a contract, such as pricing or schedules.
- Controlled Unclassified Information (CUI): more sensitive material like technical data, blueprints, or research details, that must stay protected.
The more sensitive the data, the higher your required CMMC level.
What is a “Control” in CMMC?
- Using strong passwords is a control.
- Encrypting sensitive files is another control.
- Keeping your software updated is also a control.
The Three CMMC Levels Explained
The CMMC framework is divided into three levels, each designed for different types of defense contractors and data sensitivity.
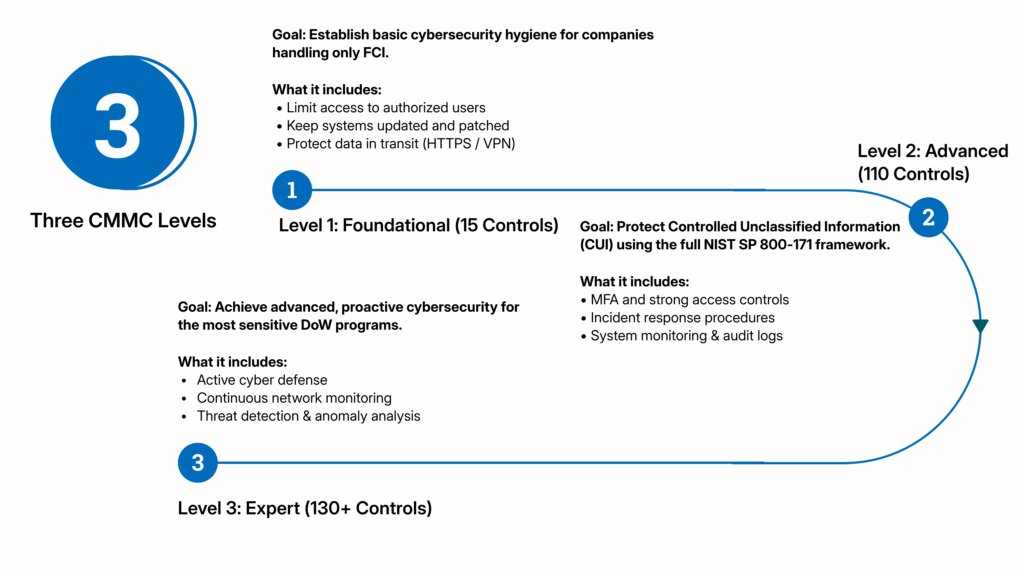
Level 1: Foundational (15 Controls)
Limiting system access to authorized users
Updating software and applying security patches
Protecting information during transmission
Physically securing workstations and devices
Training employees on safe practices
Level 2: Advanced (110 Controls)
Multi-factor authentication (MFA) for user access
Incident response procedures and reporting
Audit logging and system monitoring
Encryption of stored and transmitted data
Periodic security assessments and reviews
Level 3: Expert (130+ Controls)
- The DoW has not yet broadly mandated Level 3 for all contracts. Level 3 is intended for the most sensitive programs.
- Because of that, the full “enforcement schedule” for Level 3 is still rolling out: which contracts will require it and when is still being phased.
- While controls and assessment guides are published, many companies are preparing for Level 3
Active cyber defense operations
Detecting and responding to sophisticated threats
Continuous monitoring of network activity
Advanced encryption and anomaly detection
Insider threat programs and incident simulation
How to Identify Your Level
The easiest way to determine your level is to ask two key questions:
Do you ever receive or create information labeled “CUI”?
Does your contract reference DFARS 252.204-7012 or NIST SP 800-171?
If it does, that means CUI is in scope → Level 2 applies.
When in doubt, the DoW’s rule of thumb is simple: protect what you touch.
If your systems touch CUI, you must secure them under the correct level of CMMC.
Transparent CMMC Pricing That Fits Your Level
At Cyber Security Solutions (CSS), we help contractors meet exactly the level that applies – no upsells, no inflated packages, no jargon.
Our pricing is fully transparent and scales with your team size and compliance scope:
Startup Plan — $200 / month / device (Level 1)
For small businesses handling only FCI. Covers up to 3 devices with managed firewall, VPN, SOC monitoring, encryption, and compliance dashboard.
CSS Enclave Plan — $1,250 / month (Level 1 & 2)
For growing teams (4–10 devices) needing full Level 2 alignment and 24/7 U.S.-based SOC support.
CSS Net Plan — $2,100 / month (Level 2 readiness)
For larger organizations (11–25 devices) needing continuous monitoring, documentation management, and enterprise-level control.
Ready to close your business gap?
Schedule a meeting with an expert