Compliance and Security Provided by Cyber Security Solutions
Healthcare Cybersecurity
HIPAA & HITRUST CSF
CSS provides a seamless process to address HIPAA & HITRUST CSF requirements. From annual assessments to full remediation and monitoring packages, we do it all.
What all is Included?
- Security Hardware Infrastructure
- Security Cloud Infrastructure
- Managed Security Services
- 24/7/365 Monitoring & Helpdesk
- Compliance Dashboard
- Cybersecurity Training Program
What to know about
HIPAA & HITRUST
- HIPAA is a U.S. law that enlists safeguards that organizations and their employees must follow to protect healthcare information.
- HITRUST CSF is a certifiable security and privacy framework, with mandated controls and requirements, that can be utilized to show proof of HIPAA compliance.
HITRUST CSF Assessments
There are three different forms of HITRUST assessments to help organizations that are looking for a measure to prove their implementation and identify their risk level to ensure that PHI is secure and private. Below is a chart to provide understanding of the three different levels of HITRUST assessments.
Basic
Implemented
Risk-Based
Purpose
Use Case
Focus on good security hygiene controls in virtually any size organization with a simple approach to evaluation, which is suitable for rapid or low assurance requirements
A threat-adaptive assessment focused on best security practices with a more rigorous approach to evaluation, which is suitable for moderate assurance requirements
Focus on a comprehensive risk-based specification of controls suitable for most organizations with an attentive approach to evaluation; Meets high assurance requirements
Required Controls
(Requirements)
71 Basic Controls that focus on good security hygiene
219 Pre-Set Controls leveraging best practices/threat intelligence
2000+ based on Tailoring
(360 avg. in Assessment Scope)
Assurance Level
(Low, Moderate, High)
Low
Moderate
High
Certifiable Assessment
No
Yes (1 Year)
Yes (2 Year)
Why Choose Cyber Security Solutions?
Our assessment process is not influenced by personnel involvement and extensive questionnaires. Results reported are actual configuration settings and documented evidence showing compliance or non-compliance. Your personnel will not have to answer hundreds of questions and attend countless meetings/calls that take weeks to complete.
Once results are compiled, we schedule an out brief to discuss all non-compliance findings with evidence. You will also receive a detailed report of findings along with the tools to plan out your compliance journey. We leverage our technology to ensure the most accurate results. Also, our package includes all of the necessary documentation to start your compliance journey at very affordable cost.
Expedited Process
Our process takes much less time than majority of our competitors.
The total time (from start to finish) is typically 1 week.
Time required from your personnel is generally less than 4 hours.
Accurate Results
We utilize our scanning agents to test the configurations and settings across your entire corporate network. This not only saves time and effort of going through lengthy questionaires, it ensures accuracy.
Thorough Out-briefing
Our out-briefing is in depth, where we spend the time to ensure your team understands your areas of non-compliance. We will also briefly cover your remediation path using our CMMC Compliance Dashboard.
call today to protect your business
Talk to one of our experts today to learn how we can identify your current risks and vulnerabilities and put together a package to better protect your.
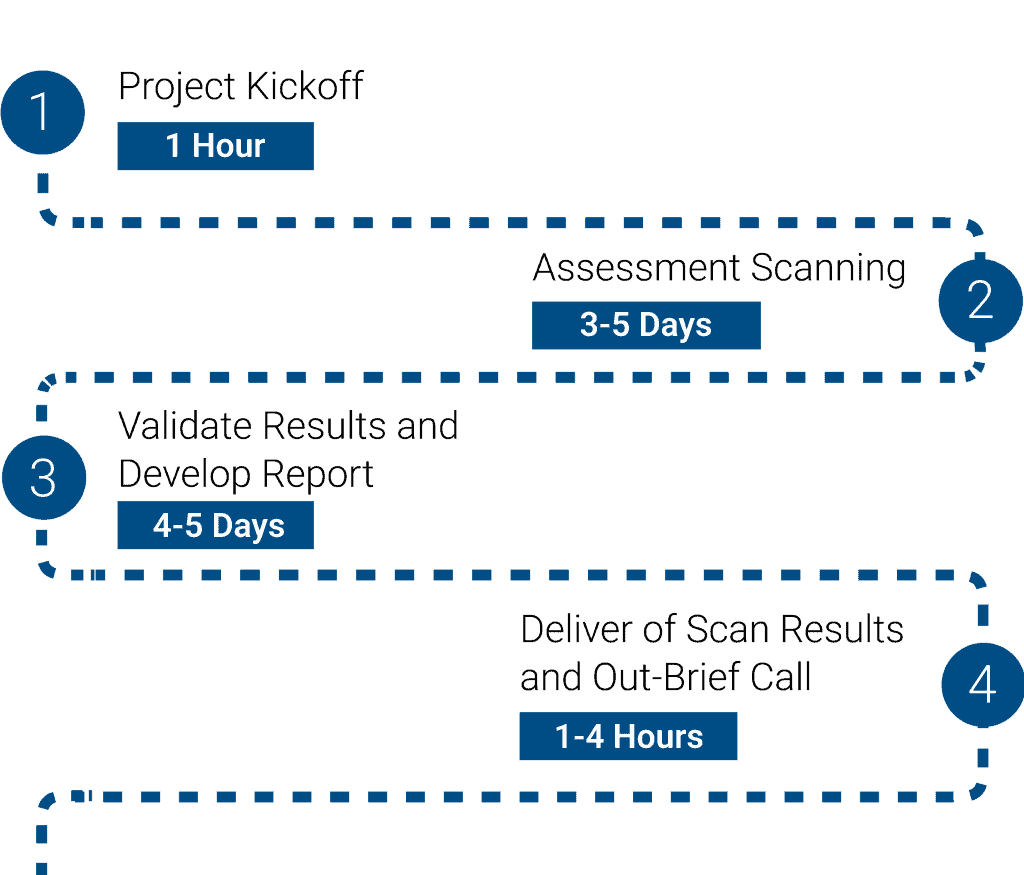
Step 2:
Assessment Scanning
Our team will deploy agents to all devices used to access your corporate network.
Power settings need to be adjusted for the scan to run overnight, as a way to not impact operations.
Scans are typically started on Friday evening and
completed by Monday morning.
Results are compiled in our Secure Vault, housed in a FedRAMP approved environment.
Step 3:
Validate Results & Develop Reports
CSS personnel will verify scan results from all devices and generate your DoD Scorecard.
Your scores and results are uploaded into the Compliance and Monitoring Dashboard where the initial SSP and POA&M is developed.
An out-brief call is scheduled with your team to discuss results and potential remediation paths.
Step 4:
Delivery of Results & Out-Brief Call
During the scheduled out-brief call, details of the assessment scan and evidence are discussed.
Questions for required controls that could not be scanned will be discussed and documented.
CSS provides an overview and demonstration of the CMMC Compliance Dashboard, and discusses potential remediation plans to meet compliance.
Overview:
Final Deliverables
Full NIST/DFARS Compliance Assessment
DoD Assessment Scorecard
NIST SP 800-171/CMMC Compliance Scores
Initial System Security Plan (SSP)
Initial Plan of Actions & Milestones (POA&M)
PIEE/SPRS Education & Assistance
Step 1:
Project Kickoff
Once all documentation is complete (NDAs, contracts, etc.), we schedule a kickoff meeting to discuss the process and answer questions.
Information Request Forms help us identify all
devices that are in scope for the assessment.
The assessment is non-invasive, and we can assure data never leaves your network.
Our Process
Our process starts with a project kickoff, where your team will work with our Onboarding Coordinator to provide access to your corporate devices. Our scanning agent is non-invasive, and your data never leaves your network. After we complete the scanning process we will validate all results and begin to develop your reports.
The out-briefing call is an in depth overview of everything that we found. This provides a deep understanding of the work ahead to implement NIST SP 800-171 Rev 2 requirements. The entire process typically takes 1 week from start to finish, and generally requires less than 4 hours of touch time from your personnel. Hover over each number on the flowchart to read more about our process.
Our Process
The US Department of Health and Human Services (HHS) has issued the Health Insurance Portability and Accountability Act of 1996 (HIPAA) mandate requiring every Covered Entity and Business Associate that has access to PHY must ensure the technical, physical.The US Department of Health and Human Services (HHS) has issued the Health Insurance Portability and Accountability Act of 1996 (HIPAA) mandate requiring every Covered Entity and Business Associate that has access to PHY must ensure the technical, physical.The US Department of Health and Human Services (HHS) has issued the Health Insurance Portability and Accountability Act of 1996 (HIPAA) mandate requiring every Covered Entity and Business Associate that has access to PHY must ensure the technical, physical.
Final Deliverables
• Full Compliance Assessment of Client's corporate environment
• DoD Assessment Scorecard & NIST SP 800-171/CMMC compliance scores
• Initial System Security Plan (SSP) & Plan of Actions & Milestones (POA&M)
• 1 year subscription to the CSS Compliance and Monitoring Dashboard
• Assistance/walkthrough (via Screen share) of submitting a score in PIEE/SPRS
Potential Remediation Services
In our Healthcare Compliance Packages.
While these services are not included in our HIPAA/HITRUST Assessment packages, we do have Security and Compliance packages that include everything your team will need to meet HIPAA compliance. Click on any of the 30 services below to read more about what we provide as a part of our turn-key implementation packages:
We provide your full security hardware infrastructure through our Cyber Threat Compliance (CTC) platform. Our CTC includes everything from a compliant Firewall, IPS/IDS, Forward/Reverse Proxy, SIEM, and more.
Our Secure Vault platform offers a full cloud, filesharing, and collaboration tool located in our FedRAMP approved cloud environment. Our hybrid approach ensures maximum business uptime.
We develop your set of CMMC policies and procedures, reinforcing your organization’s security and compliance programs. We maintain them as requirements evolve, allowing you to focus on growing your business.
Our Compliance Dashboard provides leadership with a clear understanding of where your organization is along the compliance journey. Our documentation and reporting tools make C3PAO assessments a breeze.
Our team of expert Security Analyst are monitoring your corporate network around the clock to stop cybercriminals from infiltrating your network. CSS handle's all of the logging and reporting for you.
Can't connect to the printer? Email is down? Our experienced Help Desk team not only responds to client reported issues, but we often take care of issues before your team even notices.
We offer Security Awareness, Insider Threat, and Role Based User Access annual training modules to keep your team up to speed and within compliance. We also conduct phishing campaigns to keep your team ready.
Our Firewall as a Service provides the first layer of defense against all attacks. We handle the licensing, management, and security of our proprietary CTC platform where the firewall resides.
Our SIEM continuously monitors and acts upon real-time security information from virtually any source. We aggregate data from across your entire network, and analyze this data together to limit false-positives.
We provide all users with Multi-Factor Authentication (MFA) to ensure that the process of signing into your corporate systems is secure. We add in the benefit of Single Sign-On (SSO) to simplify your daily workflow.
We complete a full compliance assessment of your organization to measure gaps in NIST SP 800-171 and CMMC requirements. Results are imported into our Compliance Dashboard for live progress tracking.
The worst type of risks are the ones that have yet to be
identified/addressed. We work with you to understand the current state of your security posture and explain the business or financial impact of associated risks.
Our Exposure Assessment monitors external communications to your infrastructure and compares the detected communications and attempted attacks with vulnerabilities detected in our Vulnerability Scan.
Our vulnerability scan illuminates the unknown. We leave no stone left unturned; this scan enables the detection of devices, services, and vulnerabilities that were running without the knowledge of your team.
Our secure storage solution is security enforced, SOC monitored, and Disaster Recovery supported. Our team will perform automated synchronization through scheduled or continuous backups, that fit your needs.
Our Secure Backup service provides desktops with a means of file protection from natural disaster and ransomware. We ensure that your company's most important types of files are not lost in an incident.
Our Email Filtering ensures everyone operates in a secure/compliant manner. We protect you from malware and spam, as well as advanced threats like targeted spear phishing and ransomware.
Our Web Security service can be used to limit use of certain websites or block them entirely on corporate networks. This adds a layer of defense to your data by preventing the clicking of known malicious links.
Our Data Encryption service provides necessary device level data protection for security and compliance. We ensure your data remains secure and reduce the change of interception by unauthorized viewers.
Patching is a standard and well known requirement that many IT companies offer for an additional fee. We don't charge anything extra to provide this necessity since it's a compliance requirement and good practice.
Anti-Virus/Anti-Malware from CSS will always ensure that the latest attack prevention methods are in place on all endpoints, while managing any and all vendors required to provide the security.
Our VPN solution enables company owned devices to access internal network services from remote locations. A trustworthy VPN will secure and encrypt your internet, keeping data safe from malicious eyes.
Our Disaster Recovery service provides a means of file restoral and services on protected servers. We provide a complete service restoral in our cloud in as little as 4 hours, even if complete server hardware loss occurs.
Incident Response provides a team of experts in response to cyber incidents as required by regulatory compliance. We quickly determine the source, cause and extent of a breach, to include proper reporting.
Every incident is investigated and categorized, executed, and notified; all while being tracked using our After Actions Reports. Our After Actions Report is used to prove compliance requirements.
Our Reporting Platform enables decision makers to to help make cost saving decisions. Managers can prioritize replacement of the most troublesome equipment and increase workforce productivity.
Data Destruction is required for compliant disposal of assets that once held CUI. We ensure that your data storage assets are properly wiped using standards that meet or exceed your regulatory compliance needs.
Our Remote Workforce Tool allows employees to work securely from anywhere as if they were sitting at their desk. This provides the most secure means of accessing devices from anywhere in the world.
Our Secure Chat provides employees in the office, or working remote through web application or phone app, to chat in a secure and compliant manner. Chat is a client favorite for direct and team communications.
Our team installs Microsoft Office and provides licenses to every endpoint that we protect. Everyone is familiar with Microsoft products, which is why we provide cost savings for a tool you use the most.
Additional Resources
Our team has put together a list of resources and helpful links to provide a deeper understanding as you look to understand your NIST SP 800-171/DFARS compliance status. Click on the links to download some of our additional materials or visit the applicable website to learn more. You can also click below to talk to one of our experienced team members to hear more about our packaged offerings.

